Lo-Fi | Local File Inclusion
Overview

Lo-Fi is an easy TryHackMe machine made by cmnatic. This machine hosts a website on port 80 (http). On this site, we exploit a vulnerable parameter in a PHP page to obtain LFI on the host machine, and we use this to read the flag.
Nmap Scan
I’ll run nmap on all open TCP ports with NSE script and Service Version enumeration, this finds ports: 80,22.
1 | 💫 ~/thm/Lo-Fi/enumeration ➜ nmap -sCV -p 80,22 -v 10.10.228.244 |
There is ssh and http runnin Apache httpd 2.2.22 on Ubuntu.
Recon
80 - HTTP
Visiting the site, I am greeted with a website with pages for several genre’s of music.

Trying to use the search bar, it just appends ?search= to the page parameters, and has no real functionality. Instead, I’ll click on one of the pages:
This appends a new parameter to my URL:
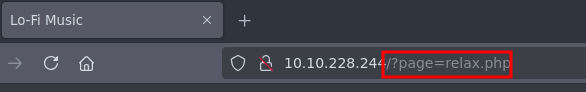
The ?page= parameter is known for being exploitable with either SSRF (Server Side Reqeuest Forgery), or LFI (Local File Inclusion). I’ll try LFI because the machine name is Lo-Fi, which hints at this being LFI:

Getting the flag
There is a filter preventing LFI, I’ll try a Directory Traversal instead:
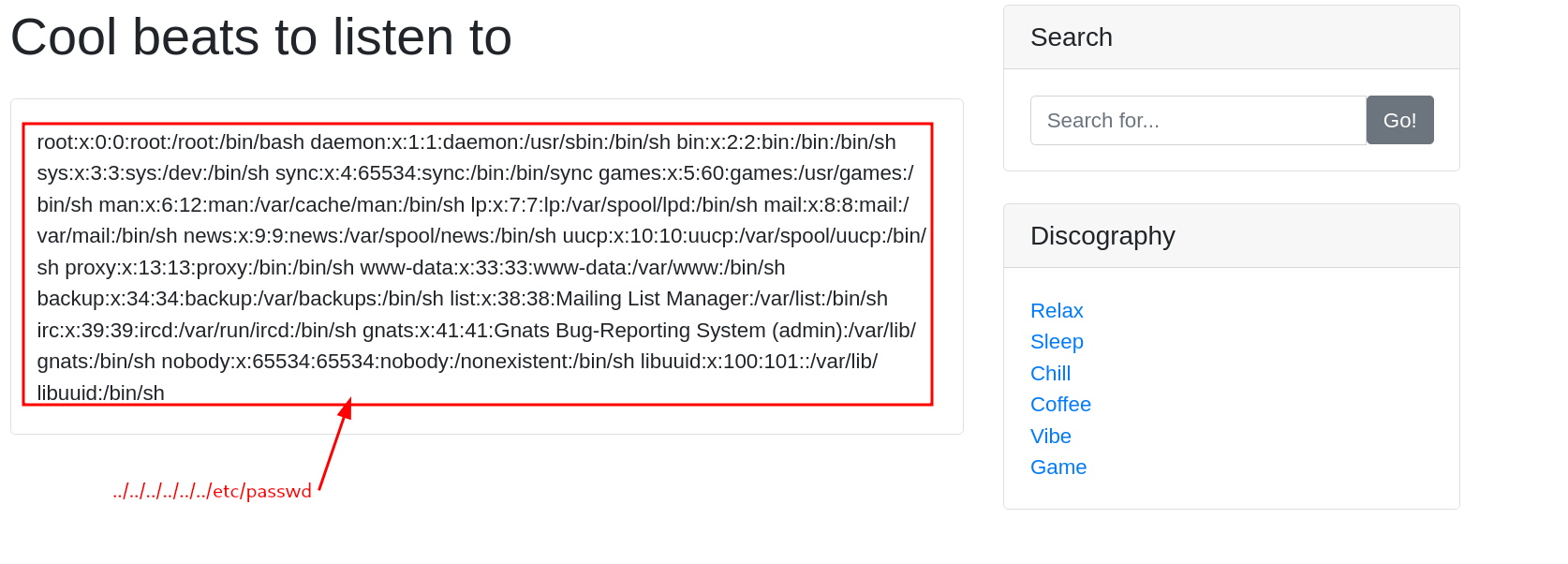
Boom! That’s LFI, I’ll use this to read /flag.txt, it’s usually there on machine’s like this:
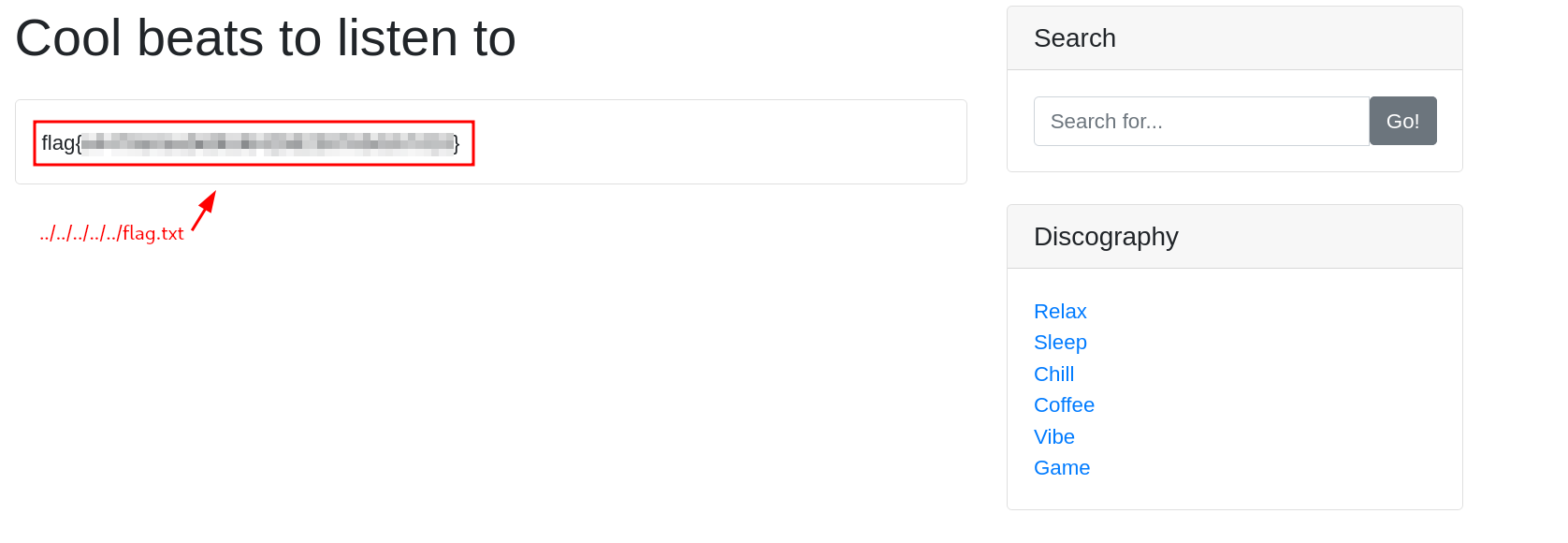
Thoughts
Overall this machine was a really good way to show beginners how to abuse LFI on a simple php site. I’d give this a 10/10, simple and straight to the point. You can read more about LFI here: https://www.invicti.com/learn/local-file-inclusion-lfi/



